Analysis: The use of open-source software by terrorists and violent extremists
Why global coding collaboration benefits everyone – including terrorists and violent extremists.
5 min read
Adam Hadley Apr 29, 2019 11:31:10 PM

On 14 April 2019, the ISIS-linked propaganda disseminator group Nashir News Agency promoted its new social media page on a relatively new social media platform called Koonekti. Within thirteen hours, the page had gathered 28 Likes and received the verified status, symbolised by the blue tick next to the page name and handle (see Fig.1). A few hours later, the page had been removed and has not reappeared since.
This is not the first case of ISIS experimenting with relatively small and lesser known social media platforms. According to BBC Monitoring jihadism specialist Abdirahim Saeed, ISIS recently tested a social media platform called Go Like, which was similarly unsuccessful. When looking at past attempts, a pattern emerges, namely the use of small- to medium-sized apps, platforms and services. Past examples are Baaz, Viber, Kik, Ask.fm, Discord and others, including micro-platforms run by a single individual.
Following the key conclusions of the European Counter Terrorism Centre's (ECTC) Advisory Network Conference at Europol, experts agree that terrorist groups carefully assess platforms and choose to settle on those that offer maximum:
When assessing the level of risk a tech or social media company faces from exploitation by terrorists, these factors should be considered.
Besides exploiting non-decentralised platforms, there are also more sophisticated efforts aimed at exploiting the benefits of emerging, data privacy-focused trends, such as the decentralised web (DWeb) and decentralised applications (DApps). The aim of these experiments is to find out whether the DWeb and DApps could provide a stable and viable alternative to Telegram. In this regard, it should be noted that decentralised platforms are inherently more difficult to monitor because the DWeb promises control and privacy for anyone using it.
Decentralised services have already been exploited by ISIS and its supporters. Examples include DWeb services Riot, ZeroNet and most recently Minds, an open source and decentralised platform. If implemented successfully and accepted by the wider pro-ISIS audience, it will become difficult - if not impossible - to tackle ISIS presence on these decentralised services. That is because these services are independent from any intermediary or ‘middle man’ for receiving and sending messages.
|
Exploiting medium- to large-sized platforms as well as DWeb services is not the only problem. In fact, there are hundreds of small- and micro-platform exploited by ISIS. From file-sharing and streaming services to pastebins, these sites have become an integral part of the propaganda distribution ecosystem. Unlike the larger platforms, small- and micro-platforms lack the required resources to tackle this exploitation alone.
At Tech Against Terrorism*, we have monitored terrorist use of the internet since 2016, and have collected more than 45,000 URLs that lead to numerous websites hosting terrorist material. Whilst this material is not a comprehensive collection of terrorist content disseminated on the internet, it provides several important diagnostic insights. Based on our analysis, we have found evidence of more than 330 platforms being used by terrorist groups within this timeframe. These platforms differ in terms of size and use-case, e.g. communication, file sharing, hosting, etc. Most importantly, we have found a stark over-representation of small- and micro-platforms amongst terrorists’ platforms of choice. For example, out of the top 50 most used platforms identified in our data, half are small- or micro-platforms (Fig.2). Also, 44% of the top 50 most used sites are file-sharing sites and other cloud storage services.
Terrorist groups have also favourite platforms: 49% of URLs were found on just eight platforms (Fig.3). The remaining 50% of content is spread across the remaining 322 platforms (98% of the long tail). This wide distribution and fragmentation of content has become more prominent in recent years, especially as some of the larger platforms have made strides in removing terrorist content and accounts from their sites.
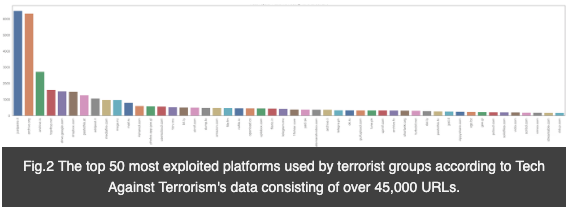
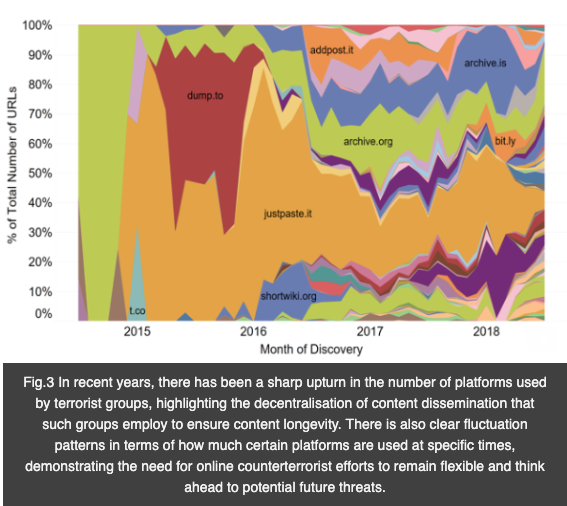
While larger platforms have undoubtedly improved their response in tackling content created by ISIS and its supporters, the smaller platforms now require significantly more support. As our analysis has shown, 25 of the top 50 most-used platforms are small- or micro-platforms. Put simply, half of ISIS’ favourite platforms (since 2016) were created and run by individuals or a small group of individuals, who often lack the financial and technical resources required to make their platforms less appealing to ISIS. This is why any response to terrorist use of the internet will need to be a systems-based approach. In other words, any response needs to view the problem as a whole and must not reduce it to just a few specific platforms.
To identify those that need support it is crucial to continue monitoring ISIS’ media operations. In doing so, research needs to focus more on the distribution ecosystem and its individual components than on the propaganda material itself. This does not mean that ISIS material should not be subjected to critical scrutiny or exploited for intelligence analysis purposes; however, to successfully disrupt the propaganda distribution system, a thorough understanding of the ecosystem, its single components and their complex, dynamic interactions is required. Any successful disruption operation would then need to target these key components of the ecosystem which have been identified as most influential in terms of containing the spread of terrorist material. However, it is important to stress that any action against ISIS media ecosystem could lead to unwanted consequences, such as a ‘mass migration’ to the DWeb or other services and apps. Additionally, the current debate around terrorist use of the internet has to be broadened to include the DWeb and its use by terrorists.
The Tech Against Terrorism team, London
*With special thanks to Hiroyasu Nagata for advice about URLs
and the data science team at QuantSpark
Why global coding collaboration benefits everyone – including terrorists and violent extremists.
In May of 2019 Tech Against Terrorism attended the inaugural annual conference of the Centre for Analysis of the Radical Right (CARR) - the leading...