3 min read
Analysis: New Zealand attack and the terrorist use of the internet
Claudia Wagner Mar 26, 2019 6:02:12 PM
Summary
-
-
- The global tech sector responded quickly in taking down the terrorist's so-called manifesto and videos of the attack: Facebook prevented 1.5m attempts by the general public to re-upload the attack video within the first 24hrs
-
- The majority of smaller tech platforms hosting the video and manifesto quickly removed the video and the manifesto from their platforms
-
- The Christchurch mosque attacks demonstrate that terrorist use of technology is a threat that affects the entire tech eco-system and that tech platforms are often exploited in combination
-
- Despite criticism of tech companies, several news outlets published the attack video and the manifesto on their websites - evidence shows that the livestream video only became viral after publishing by mainstream media
-
_____________________________________________________________________
Overview: The use of internet platforms
The use of internet technologies in this attack resembled the methodology of ISIS and al-Qaeda. Smaller file-sharing platforms were used with large platforms as "beacons" guiding users to outbound URLs. "Supporter networks" amplified terrorist propaganda by re-sharing and re-uploading material across an increasingly broad and fragmented range of smaller platforms.
_____________________________________________________________________
Timeline: Before, during, and after
-
-
- Upload manifesto to smaller platforms: before the attack, the terrorist uploaded his manifesto on a range of smaller file-sharing content storage sites such as MediaFire, ZippyShare, Solidfiles, and Mega.nz. These platforms have previously been used by ISIS and al-Qaeda
-
- Beacon on the larger tech platforms: At around 1:30pm local time (~10 minutes before the attack on Linwood Mosque) the perpetrator posted links to his manifesto for each of the above platforms on Facebook, Twitter, and 8chan's infamous "Politically Incorrect" channel, where he also posted a message about his apparent motivation
-
- Link to Facebook: In the post on 8chan the terrorist posted a link to his Facebook profile through which he then livestreamed the attack
-
- Re-share content: Following the attack, the video was shared on YouTube, LiveLeak, BitChute, Kiwifarms, and as a downloadable file on Torrentz. Further links to the attack were re-shared on Facebook, Reddit, and 8chan. The terrorist's manifesto also surfaced on Scribd, Reddit, and 8chan
-
- Publication on mainstream media: British tabloids the Daily Mail, The Sun, and The Mirror published the manifesto or the video on their websites
-
- Archive content: Archived versions of the terrorist's Twitter page, Facebook page, and 8chan post appeared on Archive Today, and a version of the MediaFire manifesto entry was archived on the Internet Archive's Wayback Machine, although the manifesto is now not available
-
_____________________________________________________________________
Tech Against Terrorism on Al Jazeera English
_____________________________________________________________________
Tech responses: Larger platforms
-
-
- Facebook: In a tweet on 16 March, Facebook said that it removed 1.5m videos of the attack within the first 24 hours - 1.2m were automatically blocked on upload. Two days later, Facebook reported in a blogpost that the video was viewed fewer than 200 times during original broadcast and that they had taken more than 800 hashes of the video to more easily detect future uploads across Facebook and Instagram
-
- Youtube: On 18 March, YouTube said it has removed tens of thousands of videos and terminated hundreds of accounts glorifying the attack, whilst reporting that the volume of videos uploaded to YouTube in the first 24 hours was "unprecedented in both speed and scale."
-
- Global Internet Forum to Counter Terrorism (GIFCT): The GIFCT said that they had hashed "800 visually distinct videos related to the attack" in their collective database
-
_____________________________________________________________________
Tech responses: Smaller platforms
-
-
- Reddit banned the main channel used to share the video. LiveLeak, one of the platforms allegedly threatened with being blocked in New Zealand for not removing the video, announced on 17 March that they will remove any version of the video uploaded on their site
-
- Generally, smaller platforms reacted responsibly to the attack. For example, Mega and Solidfiles removed the manifesto URLs citing Terms of Service (ToS) violations. MediaFire, Scribd and ZippyShare removed the manifesto. Scribd should be commended for explicitly prohibiting terrorist usage of the platform in their ToS
-
- Live4 has removed the video from their website, whilst also releasing a statement condemning the terrorist’s usage of their service, vowing to do “whatever is humanly possible” for it to never happen again
-
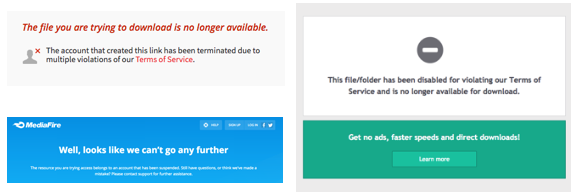 Screenshots of take down notices on Mega (top left), MediaFire (bottom left) and Solidfiles (right)
Screenshots of take down notices on Mega (top left), MediaFire (bottom left) and Solidfiles (right)
_____________________________________________________________________
Recommended action: Smaller platforms
-
-
- Despite positive action from the majority of platforms, some failed to act responsibly. Platforms that have a history of hosting questionable content still have active links to the manifesto and the full video. Platforms of potential concern include video hosts such as BitChute, Leekwire, Amerika.org, and Daily Stormer
-
- Archived versions of the Facebook page, Twitter page, and 8chan entry are still available via Archive Today, although access to some of the entries have been blocked in the United Kingdom at the request of the Counter-Terrorism Internet Referral Unit - these entries are still available the access via a non-UK VPN - highlighting the inefficiency of blocking content when geofenced
-
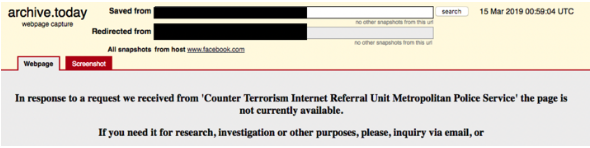
Access to some of the archived Facebook pages the terrorist used is blocked in the UK, although it is still accessible by using a VPN.
_____________________________________________________________________
Conclusions
Despite commendable action from most tech companies in the aftermath of the attack, reactive measures are not sufficient: thousands of pieces of content linked to terrorist and extremist groups are uploaded across a plethora of smaller platforms every day. Given platforms’ limited resources - and despite their best efforts - such content often remains accessible for a longer time than desirable.
The Christchurch attack shows that cross-platform responses are required. In addition to providing more practical support to platforms, we believe the international community should develop clearer guidelines on defining terrorist content and designated terrorist groups - including regarding far-right terrorism.
Press release: 10th April 2019 - Launching an updated version of Jihadology to limit terrorist exploitation of the site
10th April 2019
Press release: Tech Against Terrorism chairing the GIFCT Technical Approaches Working Group
1 May 2020
