EXPLAINER
Terrorist-Operated Websites
How terrorists and violent extremists are turning to websites to further their aims.
At Tech Against Terrorism, we have tracked and challenged a growing number of websites created to store, access and amplify terrorist content. Here we warn of the threat, and steps needed to take action.

Terrorist-Operated Websites are a key concern for Tech Against Terrorism. While terrorists and violent extremists are finding it harder to exploit social media platforms, they are finding it easier to simply set up websites for recruitment and disseminating information.
These websites operate in plain sight and despite our best efforts to have them taken down, terrorist-operated websites re-emerge due to fragmented international cooperation unclear legislation, and inconsistent responses from infrastructure providers.
In the last two years, Tech Against Terrorism have uncovered almost 300 websites operated by terrorist and violent extremist actors.
These sites are are not the exclusive practice of any single ideology or group. Violent far-right and violent Islamist groups both utilise such sites in similar ways.
In a report published in 2022, we explained how 33 of the most prominent websites – run by actors such as Islamic State, al-Qaeda, Atomwaffen Division and the Taliban – had 1.54 million monthly visitors, with the majority of visits coming from Algeria, Pakistan, United States, and the United Kingdom.
monthly visitors in 2021-22
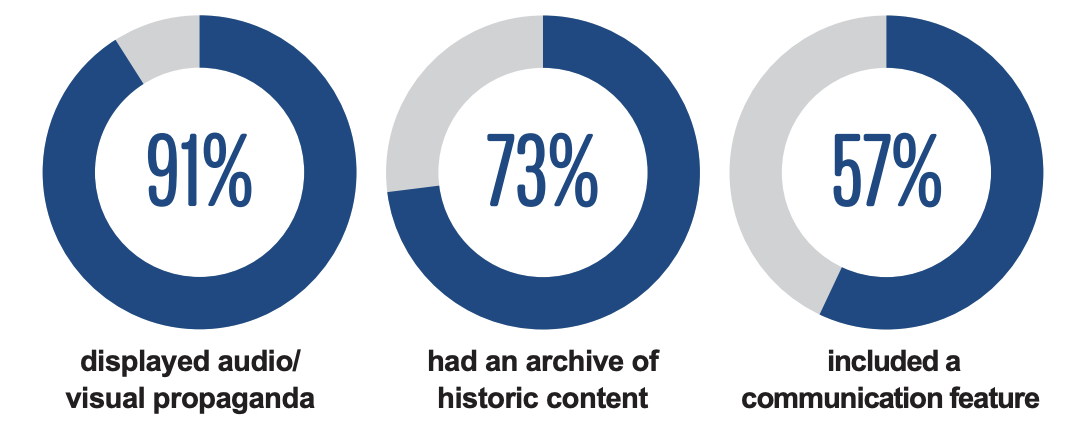
Since our 2022 report, we have monitored more websites through our Terrorist Content Analytics Platform.
Websites are easy to register, set-up and keep online. If they are detected, they can quickly reappear elsewhere following disruption.
Terrorist-Operated Websites are publicly available and are often indexed by search engines. This is partly because they are subject to little or no content sanitisation or automated content moderation.
Those setting up these websites often exploit the higher threshold for removal placed by infrastructure providers compared to social media companies.
Registrant identity can be protected and made private; some providers do not require any personally identifiable information to register, which terrorist actors regularly exploit.
The appeal of Terrorist-Operated Websites
📢 Undisturbed content distribution
📑 Archiving of content
💬 Communicating with other threat actors
💰 Generating revenue
Why this matters
Terrorist-Operated Websites offer threat actors a stable and accessible space in which to, among other activities, host propaganda content, recruit new members, and raise funds.
The proliferation of these websites are undermining counter-terrorism efforts across the industry. Their resurgence has been driven by improved tech sector responses to moderate terrorist content on social media and messaging platforms.
Yet Terrorist-Operated Websites now provide online terrorist actors with easily accessible locations where archives of content are connected to thousands of users; their existence presents a significant transnational threat.
Terrorist and violent extremist operated websites have therefore been a blind spot for policymakers, practitioners, and researchers. In our view, this risks undermining positive action taken elsewhere across the tech eco-system to disrupt online terrorist activity.
Online terrorists actors are exploiting incoherent responses to Terrorist-Operated Websites across the tech sector.
It is now time for concerted cross-sector action to close the obvious loopholes.
Tech Against Terrorism is working to provide internet infrastructure services with the context and expertise required to improve their capabilities in countering this threat.
We have also detailed recommendations for governments, regulatory bodies to adopt to stay ahead of the threat. These include:
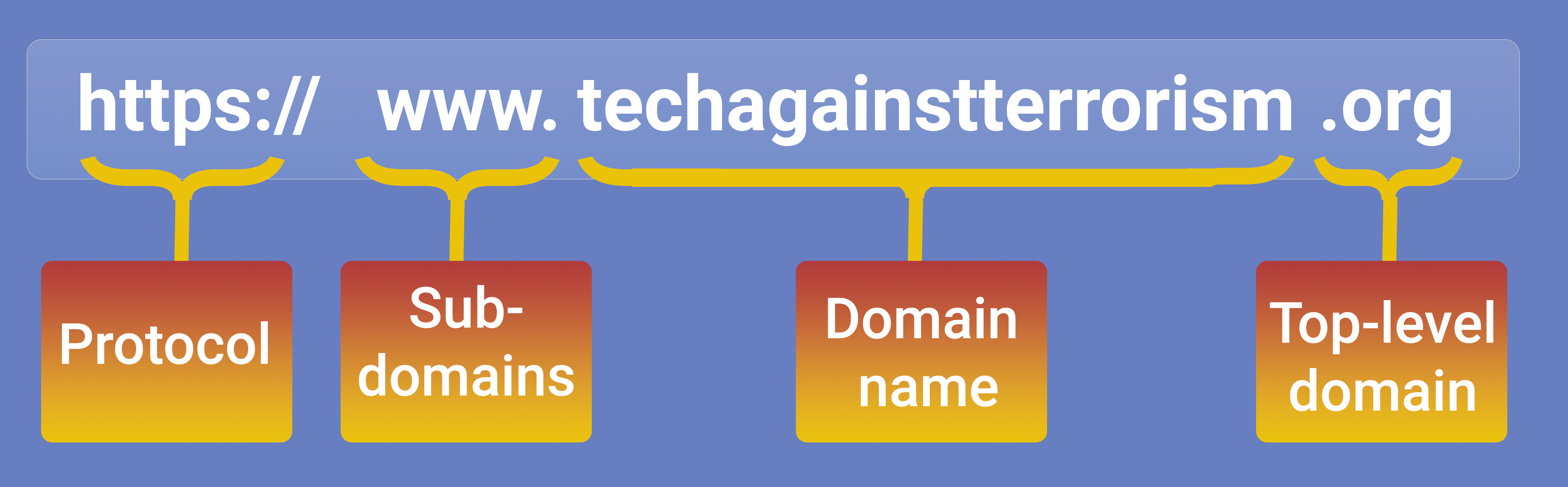
Anatomy of domains
Threat actors often rely on domain name accessibility and quickly change domain infrastructure when their sites are disrupted. This is largely due to complex technical and legal components of domain infrastructure.
Recommendations
| Governments | Infrastructure providers | Civil society |
|---|---|---|
Prioritise Terrorist-Operated Websites in policy and regulatory discussions concerning terrorist use of the internet |
Include explicit prohibition of terrorism in Terms of Service |
Increase research on Terrorist-Operated Websites and on the potential impact of their removal |
Develop a global mitigation strategy to tackle these websites by more targeted and proportionate action |
Work with governments and law enforcement to act against Terrorist-Operated Websites |
Report suspected Terrorist-Operated Websites to infrastructure providers and/or law enforcement |
Ensure that activity tackling Terrorist-Operated Websites is carried out with the fullest respect for human rights and fundamental freedoms, including for online freedom of expression |
Produce transparency reports, as recommended by Tech Against Terrorism |
Scrutinise Terrorist-Operated Website removals to ensure human rights and fundamental freedoms are not adversely impacted |
Improve the designation of terrorist groups by reference to human rights and fundamental freedom |